In the world of blockchain, each block is like a link in a chain, and it's crucial to ensure that each link is securely connected to the previous one. This connection is established using a unique identifier called a Hash. Think of a Hash as a digital fingerprint for each block.
Now, how is this hash generated? It's done using a cryptographic algorithm called SHA-256. Here's the step-by-step process:
Input Data: When new data is added to a block, whether it's a financial transaction or any other piece of information, it's sent through the SHA-256 algorithm.
Encryption: This algorithm converts the data into encrypted form. The result is a unique string of characters. Specifically, it's a string of 64 characters, each made up of 4 bits, giving us a total of 256 bits.

Hash Generation: The resulting string of characters is what we call a hash. It's essentially a unique identifier for that block. If anything in the block changes, even a single character, the hash will change completely. This makes it easy to detect any tampering with the block's data.
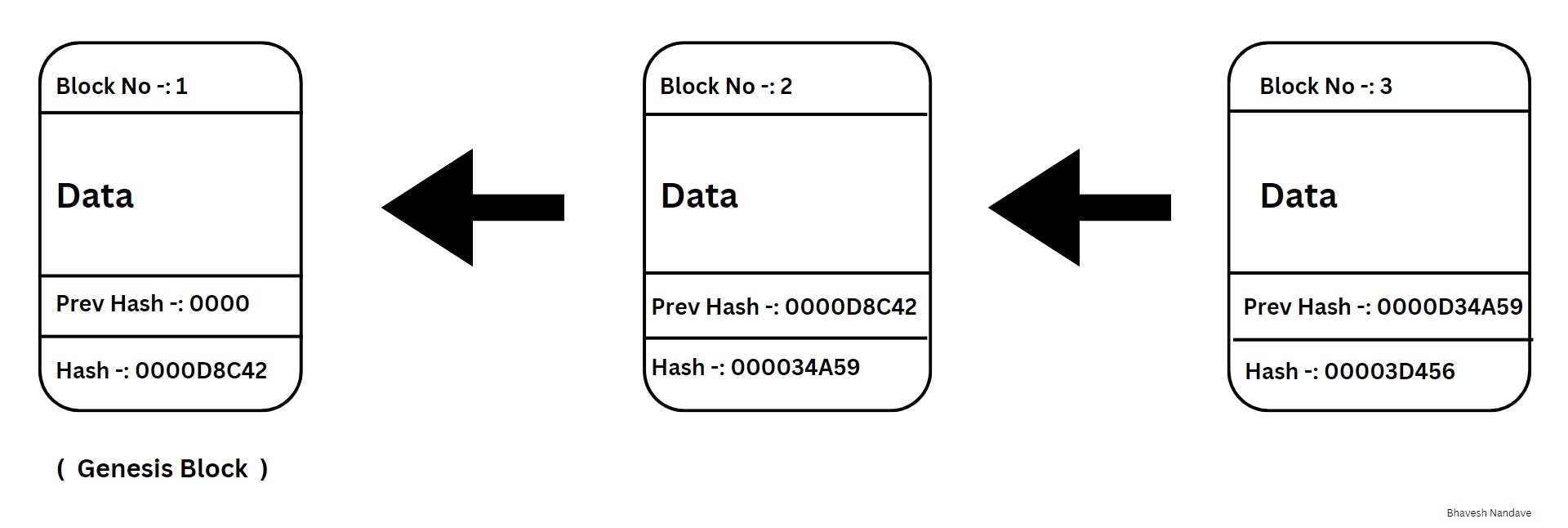
In a blockchain, each block knows the one before it. How? Well, every block has a unique ID called a hash. It's like a digital name tag.
Imagine this: Block 3 knows Block 2 because it holds Block 2's hash. Block 2 knows Block 1 in the same way. This connection creates a chain.
And guess what? The very first block in a blockchain is called the Genesis Block. It's like the starting point, the big bang of the blockchain world.
Five Requirements of a Good Hashing Algorithm:
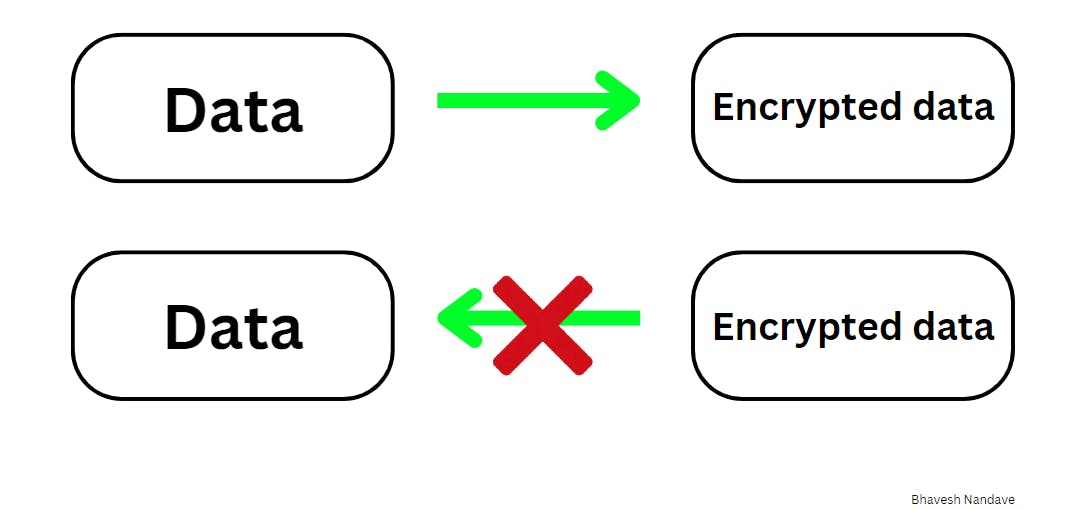
One-way: You can easily convert data into its hashed form, but it's practically impossible to reverse the process and obtain the original data from the hash. This ensures the security of the data being hashed.
eg-:
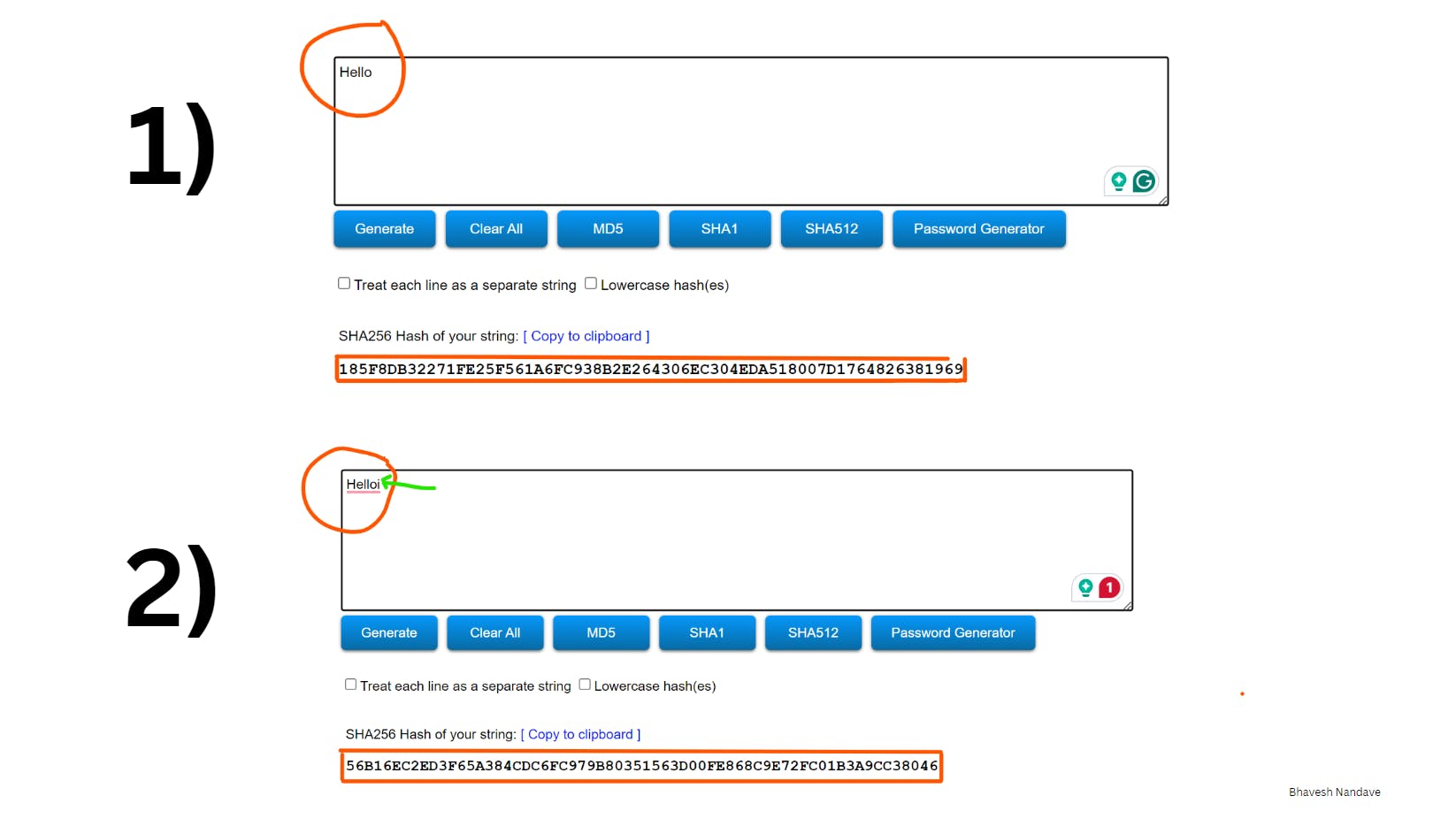
Deterministic: This means that for any given input, the output hash will always be the same. Even if you hash the same data a million times, you'll always get the same result. This property ensures consistency and reliability.
Fast Computation: Hashing algorithms need to be computationally efficient, especially in applications where hashing is done frequently, like in blockchain. The SHA-256 algorithm is designed to be fast, even for large amounts of data.
Collision Resistance: This property ensures that it's highly improbable to find two different inputs that produce the same hash output. In other words, it's extremely rare for two distinct pieces of data to have identical hash values. This helps maintain the integrity and security of the hash-based systems.
Avalanche Effect: Even a tiny change in the input data should result in a significantly different hash output. This ensures that similar inputs produce vastly different hashes, making it difficult for attackers to predict or manipulate the hash values.
eg-:
These properties collectively make hashing crucial for ensuring the security, integrity, and reliability of blockchain technology.